本项目采用 springboot+Redis的方式来实现;所采用的全部参考文献在文末,包括软件的安装、测试等等
实验环境: centos 7 安装Redis ,采用wget安装,
IDE :IDEA
配置
pom文件:
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>org.example</groupId>
<artifactId>springbootRefusePost</artifactId>
<version>1.0-SNAPSHOT</version>
<dependencies>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<version>RELEASE</version>
<scope>compile</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-data-redis</artifactId>
<version>2.3.0.RELEASE</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.67</version>
</dependency>
<dependency>
<groupId>com.fasterxml.jackson.core</groupId>
<artifactId>jackson-annotations</artifactId>
<version>2.13.1</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<version>2.3.3.RELEASE</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
<version>2.3.3.RELEASE</version>
</dependency>
</dependencies>
</project>
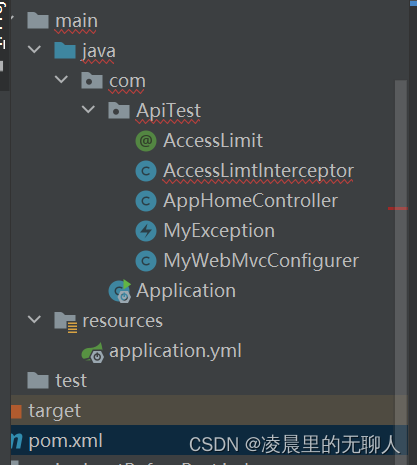
目录结构
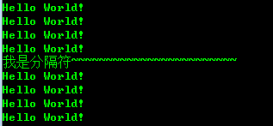
因为只测试了一个接口暴力请求,所以并没有分包,对于全局异常只是在后台抛出,并没有在前端做全局的捕获返回
飘红的原因是idea的受检异常,可忽略
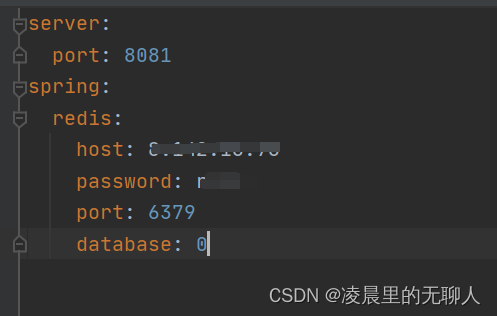
application.yml配置类
实现代码
文章中用到的六个类包括启动类如下所示:
package com.ApiTest;
import java.lang.annotation.ElementType;
import java.lang.annotation.Retention;
import java.lang.annotation.RetentionPolicy;
import java.lang.annotation.Target;
/**
* 自定义注解,用于拦截过于频繁的请求
*/
@Retention(RetentionPolicy.RUNTIME)
@Target(ElementType.METHOD)
public @interface AccessLimit {
int seconds();
int maxCount();
boolean needLogin() default true;
}
package com.ApiTest;
import com.ApiTest.MyException;
import com.ApiTest.AccessLimit;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.stereotype.Component;
import org.springframework.web.method.HandlerMethod;
import org.springframework.web.servlet.HandlerInterceptor;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.util.concurrent.TimeUnit;
/**
* 自定义拦截器
*/
@Component
public class AccessLimtInterceptor implements HandlerInterceptor {
@Autowired
private RedisTemplate redisTemplate;
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {
if (handler instanceof HandlerMethod) {
HandlerMethod hm = (HandlerMethod) handler;
AccessLimit accessLimit = hm.getMethodAnnotation(AccessLimit.class);
if (null == accessLimit) {
return true;
}
int seconds = accessLimit.seconds();
int maxCount = accessLimit.maxCount();
boolean needLogin = accessLimit.needLogin();
if (needLogin) {
//判断是否登录
}
String ip=request.getRemoteAddr();
String key = request.getServletPath() + ":" + ip ;
System.out.println(ip);
System.out.println(key);
//获取key键对应的值。
Integer count = (Integer) redisTemplate.opsForValue().get(key);
System.out.println(count);
if (null == count || -1 == count) {
//redisTemplate.opsForValue().set 增⼀个字符串类型的值,key是键,value是值。
//⽅法含义:新增⼀个字符串类型的值,并且设置变量值的过期时间。key是键,value是值,timeout 过期时间,unit 过期时间单位
//链接:https://wenku.baidu.com/view/f0de3ecc1ae8b8f67c1cfad6195f312b3169ebd1.html
System.out.println("初次进入");
redisTemplate.opsForValue().set(key, 1,seconds, TimeUnit.SECONDS);
return true;
}
if (count < maxCount) {
count = count+1;
//⽅法含义:覆盖从指定位置开始的值
redisTemplate.opsForValue().set(key, count,0);
return true;
}
// response 返回 json 请求过于频繁请稍后再试
throw new MyException("20001","操作过于频繁");
}
return true;
}
}
package com.ApiTest;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.ResponseBody;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class AppHomeController {
@GetMapping("/index")
@AccessLimit(seconds = 2, maxCount = 5) //2秒内 允许请求5次
@ResponseBody
public String getImageList(){
return "请求成功";
}
}
package com.ApiTest;
/**
* 自定义异常类
*/
public class MyException extends Exception {
// 异常代码
private String code;
//异常信息
private String message;
//构造方法
public MyException(String code, String message) {
this.code = code;
this.message = message;
}
public String getCode() {
return code;
}
public void setCode(String code) {
this.code = code;
}
@Override
public String getMessage() {
return message;
}
public void setMessage(String message) {
this.message = message;
}
}
package com.ApiTest;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.servlet.config.annotation.InterceptorRegistry;
import org.springframework.web.servlet.config.annotation.WebMvcConfigurerAdapter;
/**
* 在webconfig中配置拦截器
*/
@Configuration
public class MyWebMvcConfigurer extends WebMvcConfigurerAdapter {
@Autowired
private AccessLimtInterceptor accessLimtInterceptor;
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(accessLimtInterceptor);
super.addInterceptors(registry);
}
}
```java
package com;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.context.annotation.Bean;
import org.springframework.web.client.RestTemplate;
@SpringBootApplication
public class Application {
@Bean
public RestTemplate restTemplate() {
return new RestTemplate();
}
public static void main(String[] args) {
SpringApplication.run(Application.class, args);
}
}
到此这篇关于SpringBoot+Redis防止恶意刷新与暴力请求接口的实现的文章就介绍到这了,更多相关SpringBoot防止恶意刷新 暴力请求接口内容请搜索服务器之家以前的文章或继续浏览下面的相关文章希望大家以后多多支持服务器之家!
原文链接:https://blog.csdn.net/delete_bug/article/details/125132876